- Every thursday it’s all “About Hacking”

EVENTS Every thursday it’s all “About Hacking”
ABOUT YOU TECH
“Hacking” is one of those fields that’s somewhat a mystery even to most people working in IT. To get a better feeling for the importance of the topic and how certain attack scenarios are working in practice, we have a weekly session in the evening, that is all About Hacking. So today we kickoff the series covering our weekly Hacker-Sessions and reporting for you on all our achievements and what we learn each week.
Recap of starting sessions

We recently had our 3rd “About Hacking”-Session. Sitting all cliche together, with just a few people, in a dark corner of a meeting room, chips and beer on the side of our laptops, while starring on our screens. After our 1st and 2nd meeting where we already focused on getting our HackingEnv up and running, choosing between ParrotOS and Kali Linux and setting up a Raspberry Pi as our targeted system, yesterday it was finally time to actually start getting “our hands dirty”.
The session setup
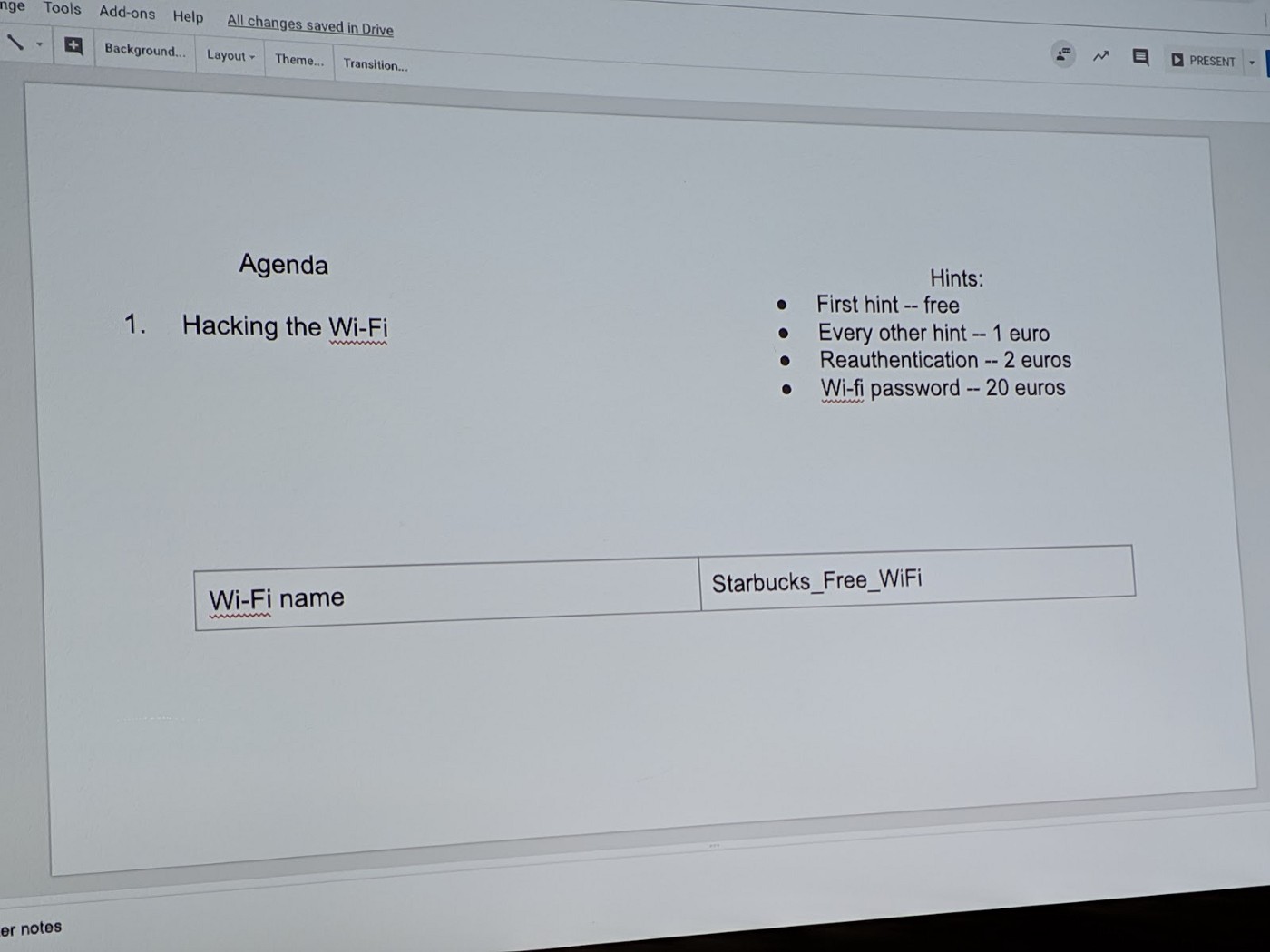
Before we get into what we did and how we did it, let’s just take a short look on the setup for each of our Sessions. Each Session will have a fixed goal to achieve after 2 ½ hours. These goals are formulated by our IT Security Team and the attack, is designed to be able to be finished within this limited time scope. Also our Security Team is providing us some resources to guide us on the way to achieving our goals.
You can get hints as well, if you are stuck but with a problem, but choose wisely as only the first will be for free. 🤔 The first to finish will get a place in our Hacking Hall of Fame, taking their place amongst Elliot Alderson, Kevin Mitnick and Edward Snowden.
To put each of these smaller attacks into a bigger picture
and frame them as a real
world attack, we organize multiple sessions into a bigger attack scenario combining multiple smaller exploits
and attack vectors.
Hacking a WPA2 Access Point
The task we got from our IT Security-Team was trying to hack into a wpa2 secured AP (Access Point) running on our Raspberry PI. We used our previously set up “Hacking” environments and got some resources to figure out the best way to do it. For some reason all of us went with ParrotOS but the tools we used ranged from all in one tools like airgeddon to some us using all tools like aircrack, hashcat and so on separately. Word of advice from me 🤓 just go with airgeddon for this specific use case, it will save you a lot of hassle.
So the basic attack for all of us worked in 5 easy steps:
- Figure out the BSSID (Basic Service Set Identification) of our target AP.
- Using that BSSID to capture all packages between the AP and all devices that are connected to it.
- Force one or multiple devices connected to the AP to reconnect to capture the handshake packages containing the encrypted WIFI-password.
- Use a dictionary file with commonly used passwords and their encrypted hash to lookup the captured, encrypted Wifi-password.
- Take password, connect to Wifi and enjoy free internet. 😁
Disclaimer
It is illegal to do this with wifis you don’t have explicit allowance for!!!
For more detailed instructions on how to do this just checkout some of our resources:
- Hacker Ethics (CCC)
- Medium article some of us used
- Video instructions on how to do this with airgeddon
- Repo with a bunch of Dictionaries
- Setup ParrotOS in vBox (VirtualBox)
- Make using ParrotOS in vBox better
Conclusion so far

“Hacking” in movies is mostly BS. Of course, we all knew or at least suspected that somehow but to actually sit down and see how an attack would work, feels so cool and it’s amazing to sit together as a group and to figure out in teamwork how to best approach these problems.
We hope you liked this inside into one of our company events and if you want to stay updated on these weekly events or any other topics surrounding About You Tech, just follow us here and any of our other channels like twitter, facebook and instagram or just go ahead and checkout some of our
open positions and take part in the next About Hacking yourself. 😎
See you there
More articles
ABOUT YOU TECH
ABOUT YOU TECH
